¶ Boogeyman 2
Date: 2025-08-10
Difficulty:Unknown|Easy| Medium |Hard
Reference: https://tryhackme.com/room/boogeyman2
¶ Scenario
The Boogeyman is back!
Maxine, a Human Resource Specialist working for Quick Logistics LLC, received an application from one of the open positions in the company. Unbeknownst to her, the attached resume was malicious and compromised her workstation.
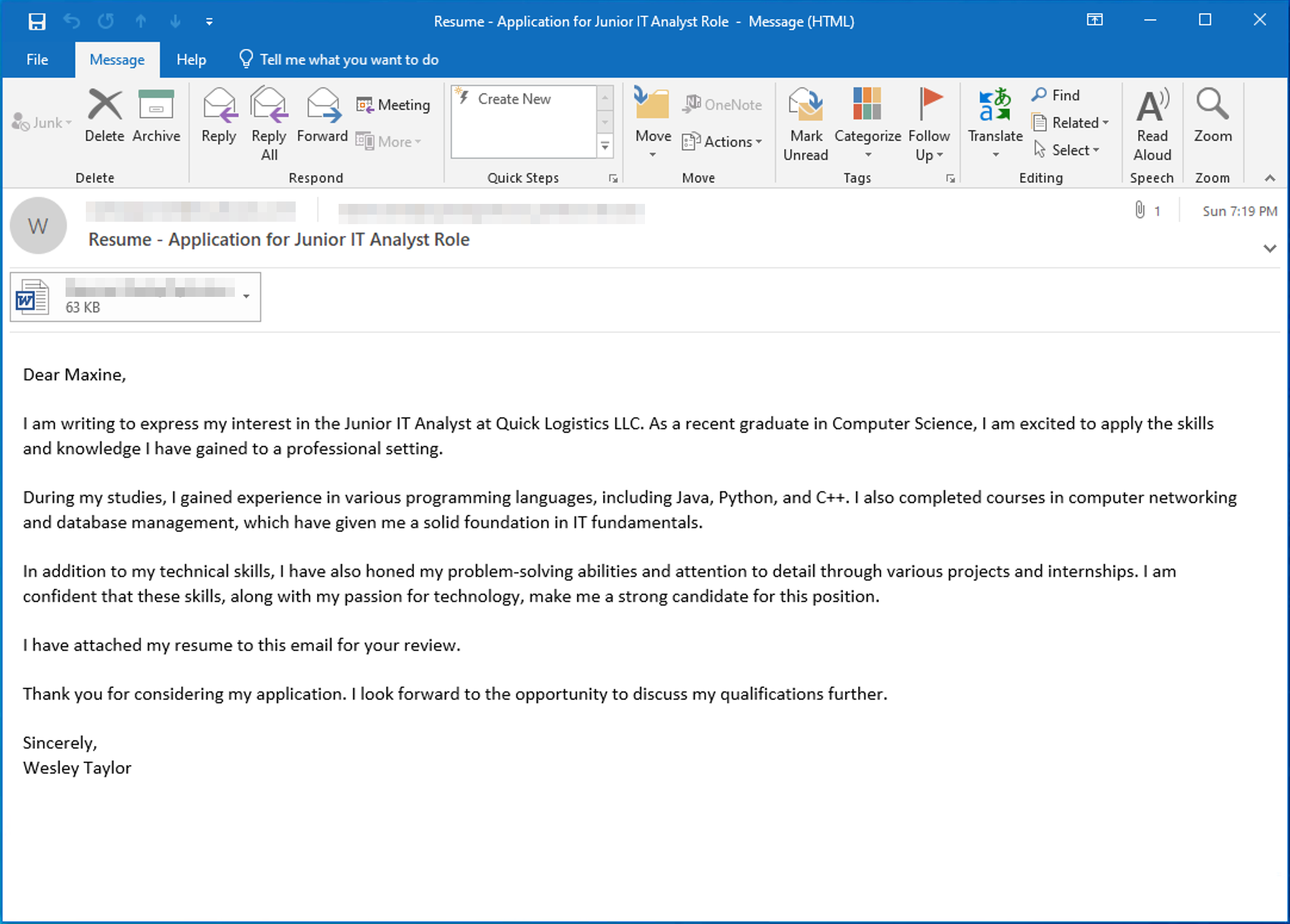
The security team was able to flag some suspicious commands executed on the workstation of Maxine, which prompted the investigation. Given this, you are tasked to analyse and assess the impact of the compromise.
¶ 1. What email was used to send the phishing email?
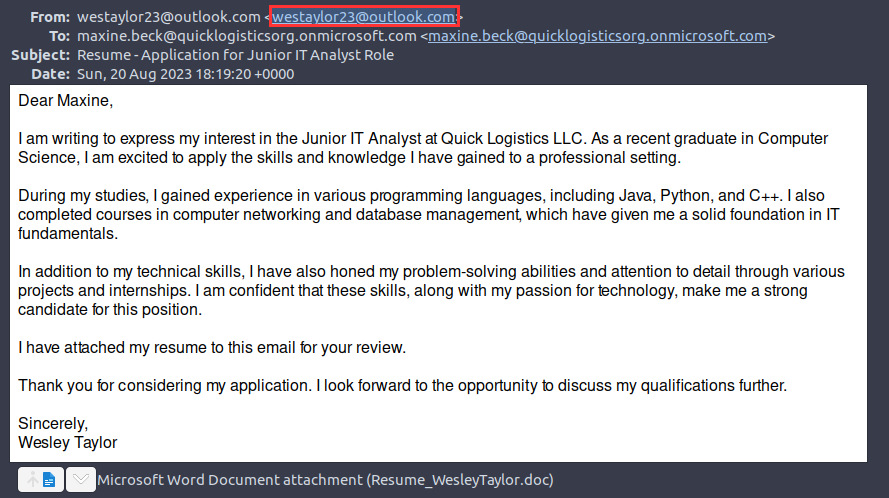
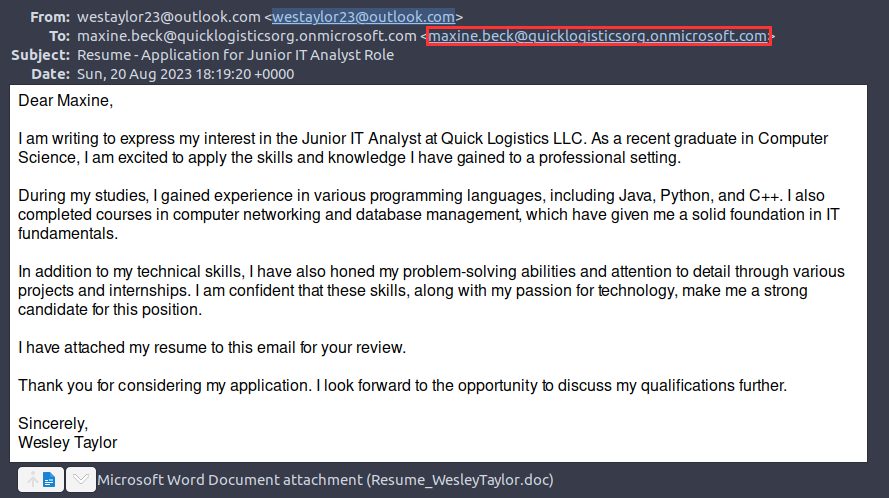
¶ 2. What is the email of the victim employee?
¶ 3. What is the name of the attached malicious document?
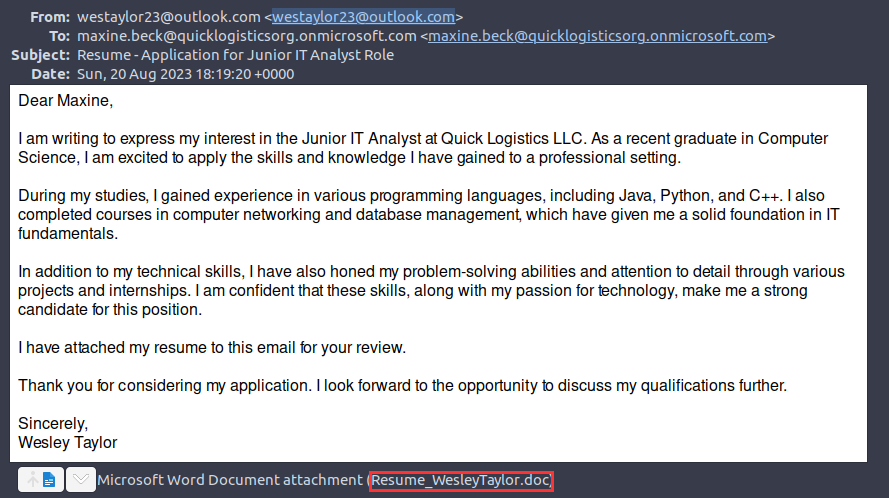
Resume_WesleyTaylor.doc
¶ 4. What is the MD5 hash of the malicious attachment?
I saved the attachment and used md5sum to get the hash:
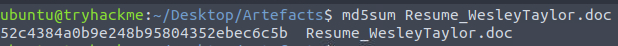
52c4384a0b9e248b95804352ebec6c5b
¶ 5. What URL is used to download the stage 2 payload based on the document's macro?
I used strings to analyze the document:
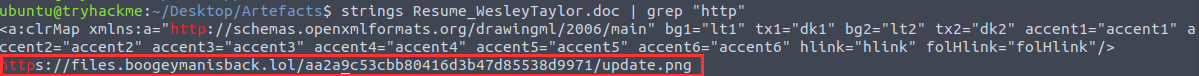
https://files.boogeymanisback.lol/aa2a9c53cbb80416d3b47d85538d9971/update.png
¶ 6. What is the name of the process that executed the newly downloaded stage 2 payload?
Using strings again, I saw that shortly after the URL from the previous question, wscript.exe was being executed:
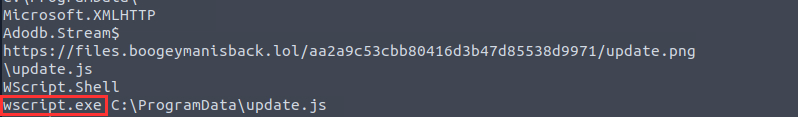
wscript.exe
¶ 7. What is the full file path of the malicious stage 2 payload?
wscript.exe executed C:\ProgramData\update.js:
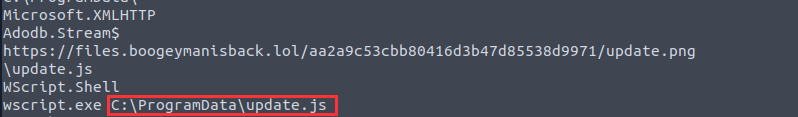
C:\ProgramData\update.js
¶ 8. What is the PID of the process that executed the stage 2 payload?
Using the memory dump "WKSTN-2961.raw" and Volatility, I ran the following command to get the running processes:
vol -f WKSTN-2961.raw windows.pstree | grep -B 10 -A 10 "wscript.exe"
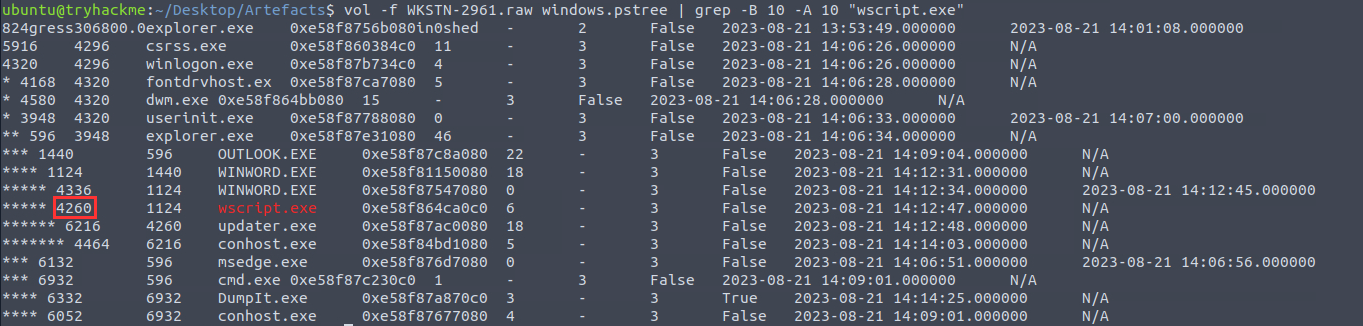
4260
¶ 9. What is the parent PID of the process that executed the stage 2 payload?
Using the pstree module of Volatility (like in the previous question), you can see the hierarchy of the processes:
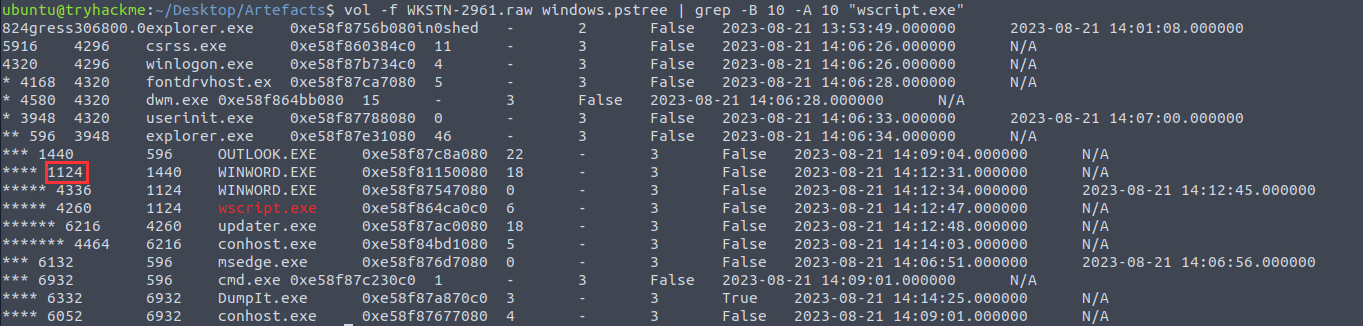
1124
¶ 10. What URL is used to download the malicious binary executed by the stage 2 payload?
I used strings on the memory dump and grepped for the domain boogeymanisback.lol from question 5:
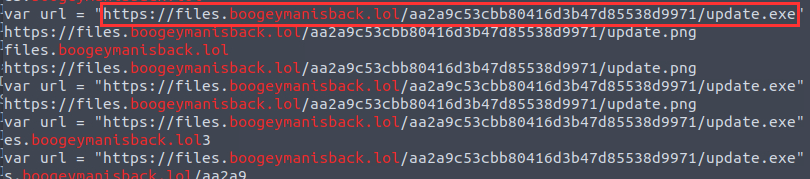
https://files.boogeymanisback.lol/aa2a9c53cbb80416d3b47d85538d9971/update.exe
¶ 11. What is the PID of the malicious process used to establish the C2 connection?
Using pstree again, you can see that wscript.exe spawned a child process updater.exe:
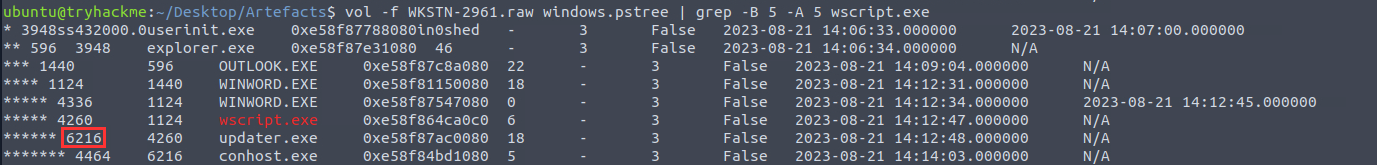
6216
¶ 12. What is the full file path of the malicious process used to establish the C2 connection?
Using the modules pslist or pstree only provides the name but not the full path. I used the windows.dlllist module to get the needed information:
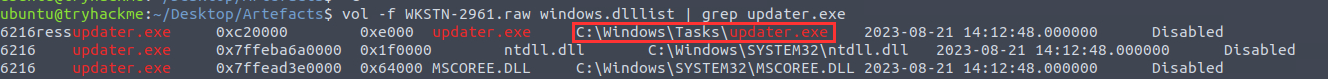
C:\Windows\Tasks\updater.exe
¶ 13. What is the IP address and port of the C2 connection initiated by the malicious binary? (Format: IP address:port)
Knowing the PID and binary of the process that initiated the C2 connection, I used netscan to get the needed information:
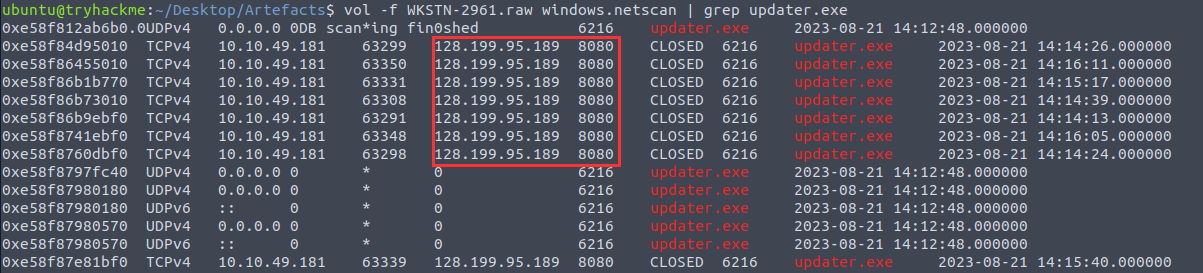
128.199.95.189:8080
¶ 14. What is the full file path of the malicious email attachment based on the memory dump?
Using the filescan module and grepping for "doc" provided the answer:
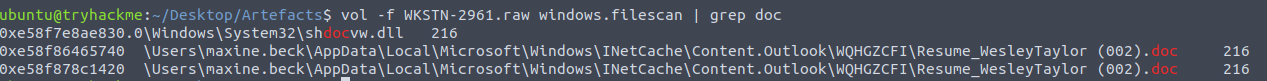
C:\Users\maxine.beck\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\WQHGZCFI\Resume_WesleyTaylor (002).doc
¶ 15. The attacker implanted a scheduled task right after establishing the C2 callback. What is the full command used by the attacker to maintain persistent access?
Using strings and grep, I filtered for schtasks, the Windows tool for creating a scheduled task:
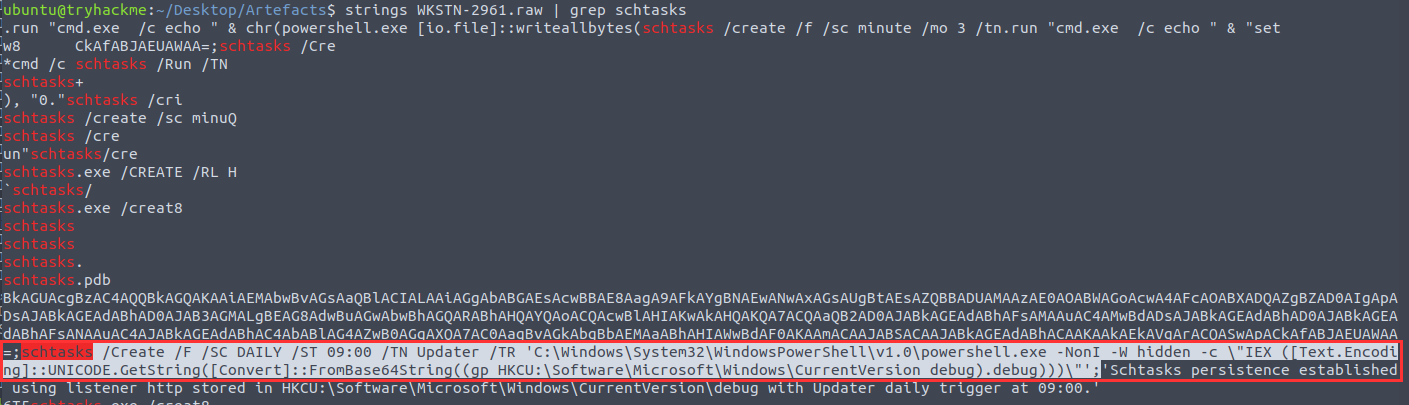
schtasks /Create /F /SC DAILY /ST 09:00 /TN Updater /TR 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -NonI -W hidden -c \"IEX ([Text.Encoding]::UNICODE.GetString([Convert]::FromBase64String((gp HKCU:\Software\Microsoft\Windows\CurrentVersion debug).debug)))\"';