¶ General Information
- Target IP:
10.10.220.25- SSH Username:
ctf- SSH Password:
ctf- Room: CTF Level One
- Date: 2025-04-22 (starting date)
¶ File System Flags
¶ 1. File System Flag
I logged into the target machine by using:
ssh ctf@10.10.220.25
According to the instruction, the first file system flag was located in a file named find_flag.txt.
I ran the command:
find / -name "find_flag.txt" 2>/dev/null
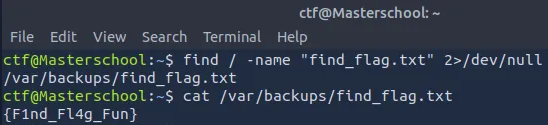
Found Flag: {F1nd_Fl4g_Fun}
¶ 2. File System Flag
With ls -a in the home directory of the user ctf, I listed all files/directories, including hidden ones. I found .f.txt, which contained the second flag.
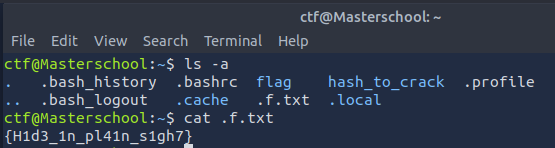
Found Flag: {H1d3_1n_pl41n_s1gh7}
¶ 3. File System Flag
In the flag directory of the home folder, there was a file named story.txt.
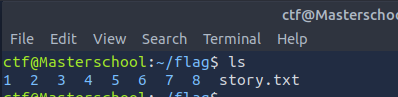
I retrieved its content with:
cat story.txt
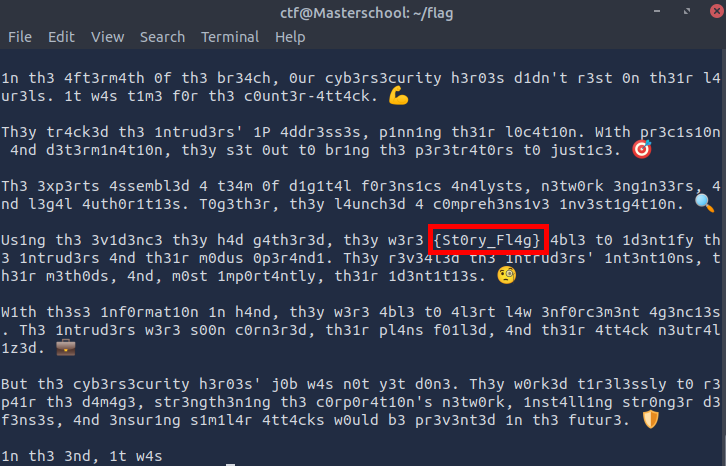
Found Flag: {St0ry_Fl4g}
¶ 4. File System Flag
In the flag directory, there were eight subdirectories. I navigated into the first one, named 1, using:
cd 1
and listed its contents with:
ls
There was another directory named d. I realized that this manual approach could go on for a while and wasn't efficient.
I went back to the flag directory and searched for files in all subdirectories with:
find . -type f
I found a file f_l_a_g.txt in flag/6/m/a/s/t/e/r/s/c/h/o/o/l/ that contained the last file system flag.
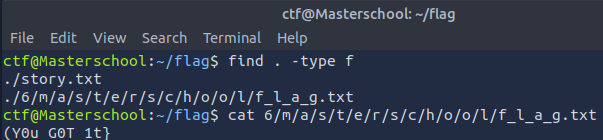
Found Flag: {Y0u_G0T_1t}
¶ Hash Flags
The directory hash_to_crack contained following files:
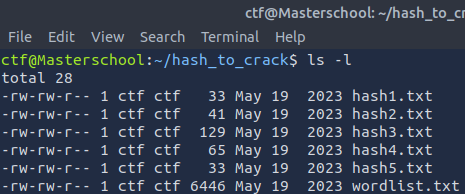
To retrieve all files, I used an FTP connection with the ctf user and downloaded the contents of hash_to_crack. Then I used tools on my attackbox: hashid to identify the hashing algorithm and john the ripper to crack the hashes.
¶ 1. Hash Flag
The hash algorithm was likely MD2, MD5, or MD4.
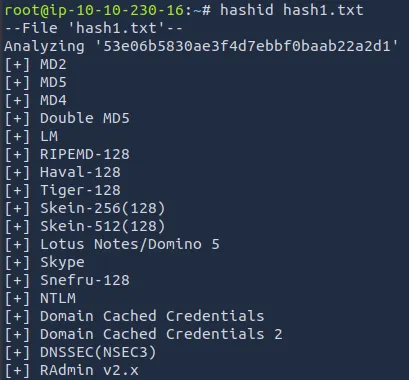
I tried MD5 first. I ran the following command using john the ripper and the downloaded wordlist wordlist.txt from the target server:
john --format=raw-md5 --wordlist=wordlist.txt hash1.txt
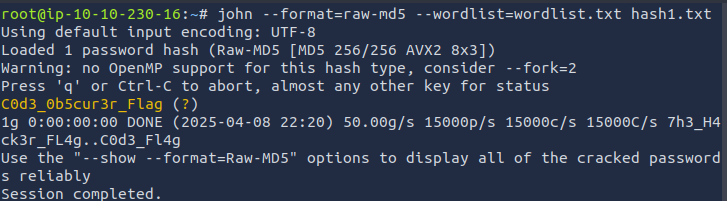
Found Flag: C0d3_0b5cur3r_Flag
¶ 2. Hash Flag
I used the same procedure as before.
john --format=raw-sha1--wordlist=wordlist.txt hash2.txt
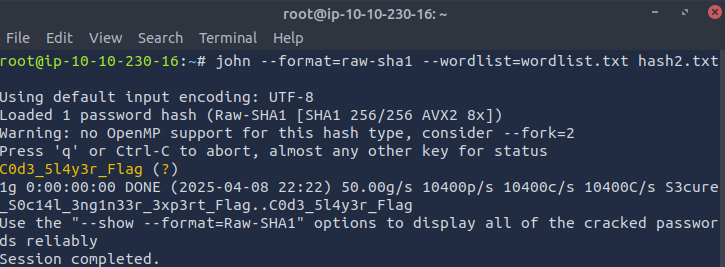
Found Flag: C0d3_5l4y3r_Flag
¶ 3. Hash Flag
john --format=raw-sha512--wordlist=wordlist.txt hash3.txt
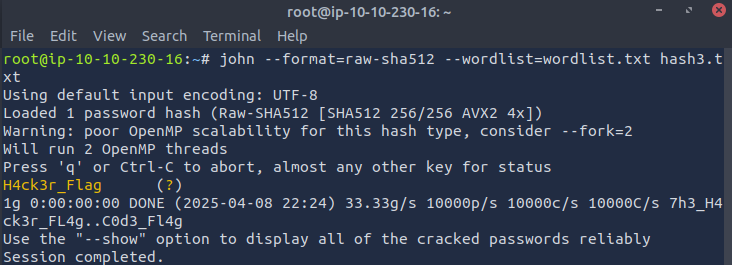
Found Flag: H4ck3r_Flag
¶ 4. Hash Flag
john --format=raw-sha256--wordlist=wordlist.txt hash4.txt
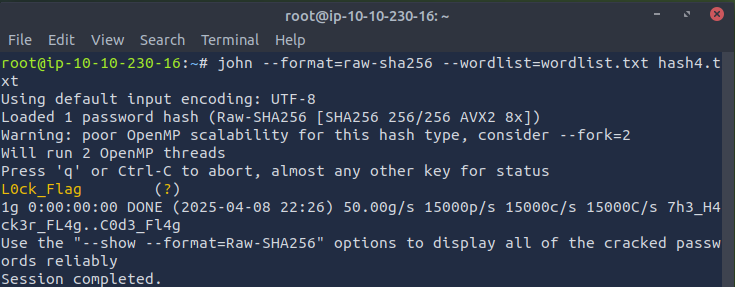
Found Flag: L0ck_Flag
¶ 5. Hash Flag
john --format=raw-md5--wordlist=wordlist.txt hash5.txt
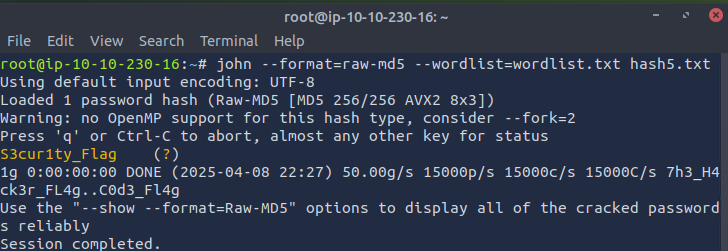
Found Flag: S3cur1ty_Flag
¶ Webpage Flags
¶ 1. Webpage Flag
I accessed the target machine in Firefox and found the first flag.
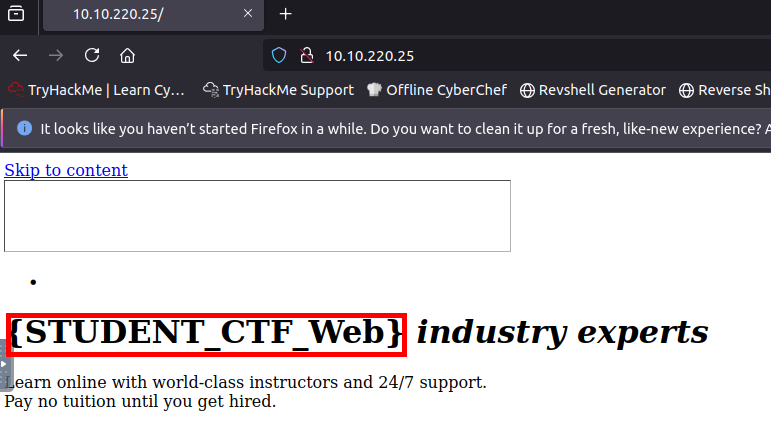
Found Flag: {STUDENT_CTF_Web}
¶ 2. Webpage Flag
I opened the development tools in Firefox (F12) and found comments in the HTML source code containing the second flag.
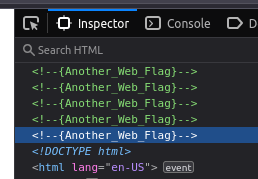
Found Flag: {Another_Web_Flag}
¶ 3. Webpage Flag
The webserver directory was located at /var/www/html. I navigated to this location via my existing SSH connection and listed all the files:
cd /var/www/html
ls
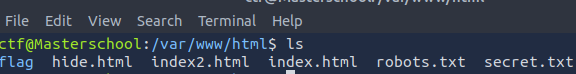
I visited http://10.10.220.25/hide.html and found the third webpage flag.
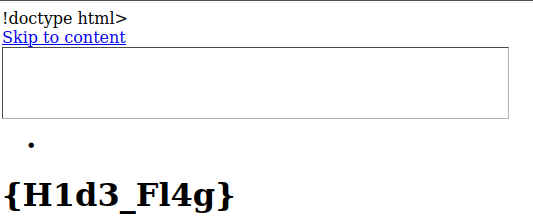
Found Flag: {H1d3_Fl4g}
¶ 4. Webpage Flag
In the /var/www/html folder, there was also index2.html. I opened it in the browser and found a modified Apache2 default page that contained the fourth flag.
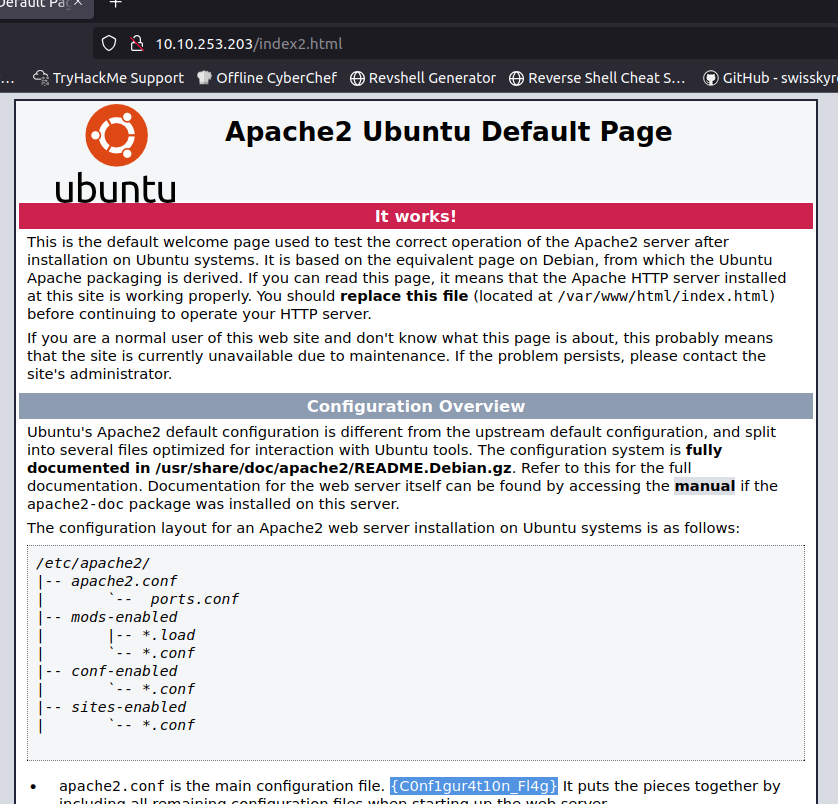
Found Flag: {C0nf1gur4t10n_Fl4g}
¶ 5. Webpage Flag
The file secret.txt in /var/www/html contained the fifth webpage flag.
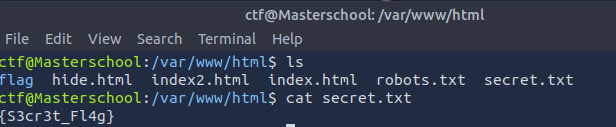
Found Flag: {S3cr3t_Fl4g}
¶ 6. Webpage Flag
The file robots.txt in /var/www/html contained the sixth webpage flag.
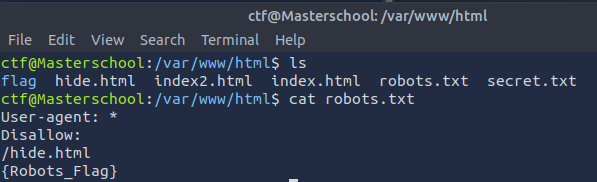
Found Flag: {Robots_Flag}
¶ 7. and 8. Webpage Flags
In the /var/www/html folder, there was a folder flag, which contained another subfolder flag with two files.
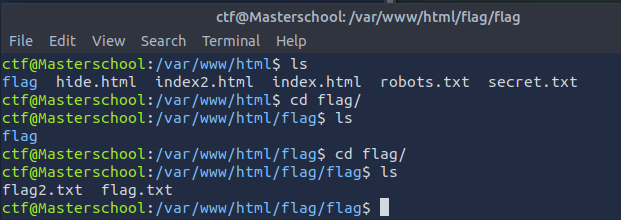
¶ 7. Webpage Flag
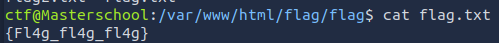
Found Flag: {Fl4g_fl4g_fl4g}
¶ 8. Webpage Flag
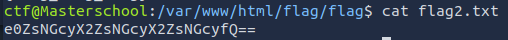
The file flag2.txt contained a base64-encoded string, which I decoded using CyberChef.
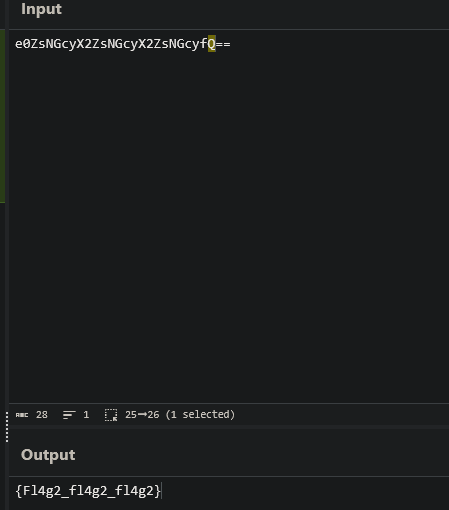
Found Flag: {Fl4g2_fl4g2_fl4g2}
¶ Other Flags
¶ 1. Other Flag
The first other flag was displayed immediately after I established a SSH session.
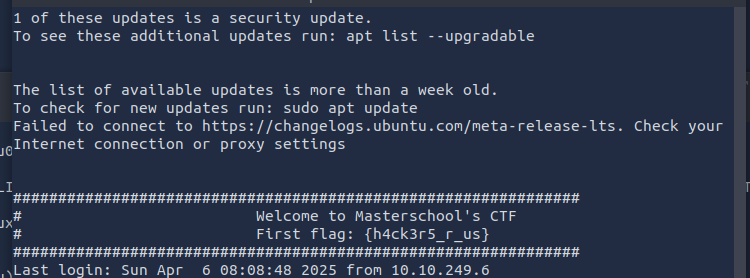
Found Flag: {h4ck3r5_r_us}
¶ 2. Other Flag
I knew from a previous task that the target server ran an FTP service. I attempted to log in as anonymous, which succeeded. The anonymous directory contained flag.txt and files.zip.
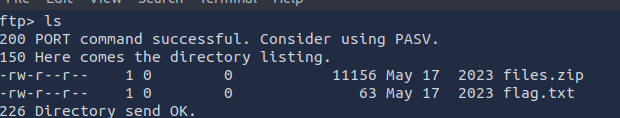
I downloaded both files to my attack box.
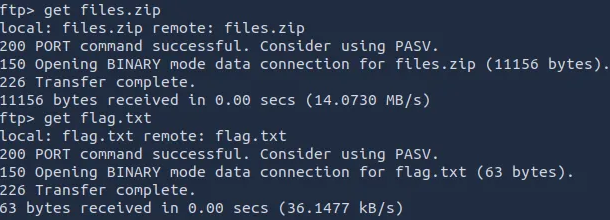
The content of flag.txt included the next flag and a hint about the zip file.
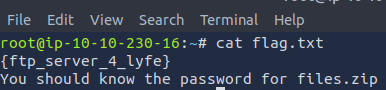
Found Flag: {ftp_server_4_lyfe}
¶ files.zip Password & John Flag
The previously downloaded files.zip archive contained secret.zip and wordlist.txt and required a password.
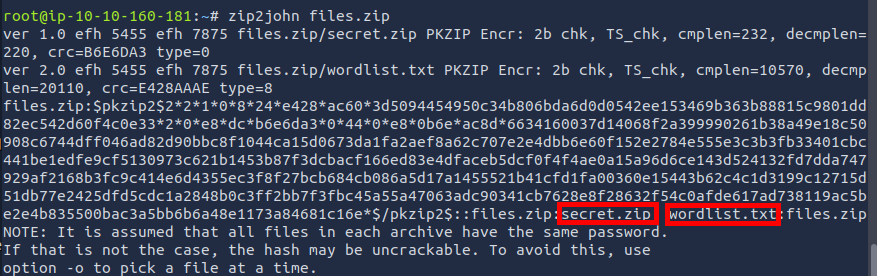
I was unsure how to obtain the password. Common wordlists such as rockyou.txt didn’t help. Also the hint from the previous flag, that I should know the the password for files.zip didn't help. After consulting with fellow students and my mentor without success, I found the password in a CTF Walkthrough: Masterschool.
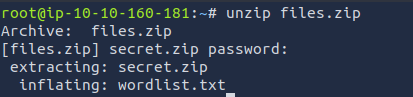
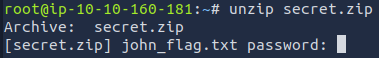
The second zip file also required a password:
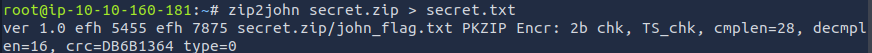
I extracted the hash of secret.zip with zip2john and saved the output to secret.txt:
Then I cracked the password using john and the extracted wordlist:
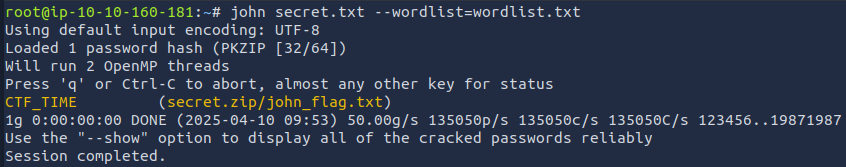
The password was CTF_TIME. I extracted john_flag.txt using this password. The file contained the last flag.
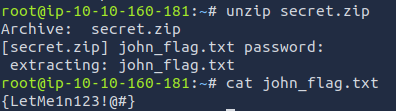
John flag: {LetMe1n123!@#}