¶ Home Lab (public)
This home lab is a sandbox for building and managing a domain environment, conducting red and blue team exercises, simulating attacks, and exploring SOC operations.
It documents hardware details, server configurations, network designs, IP plans, and internal services. Below you’ll find:
Last updated: 2025-11-25
¶ 1. Documentation Index
- Infrastructure – networking, storage, virtualization, DNS
- Servers – physical and virtual servers
- Clients – physical and virtual clients
- Services – self-hosted tools and platforms
- Monitoring – system and service health monitoring
¶ 2. Initial Setup Walkthrough
Key stages of the build process. Click to view full details:
- Network Design Draft
- Proxmox Installation
- Image Management
- VM Creation and Initial Configuration
- SPICE Setup for Desktops
- Network Design Rework
- OPNsense Installation
- Reconfigure Proxmox and pfSense
- OPNsense initial configuration
- Network Design Update
- pfSense general config
- Finish
- Lessons Learned
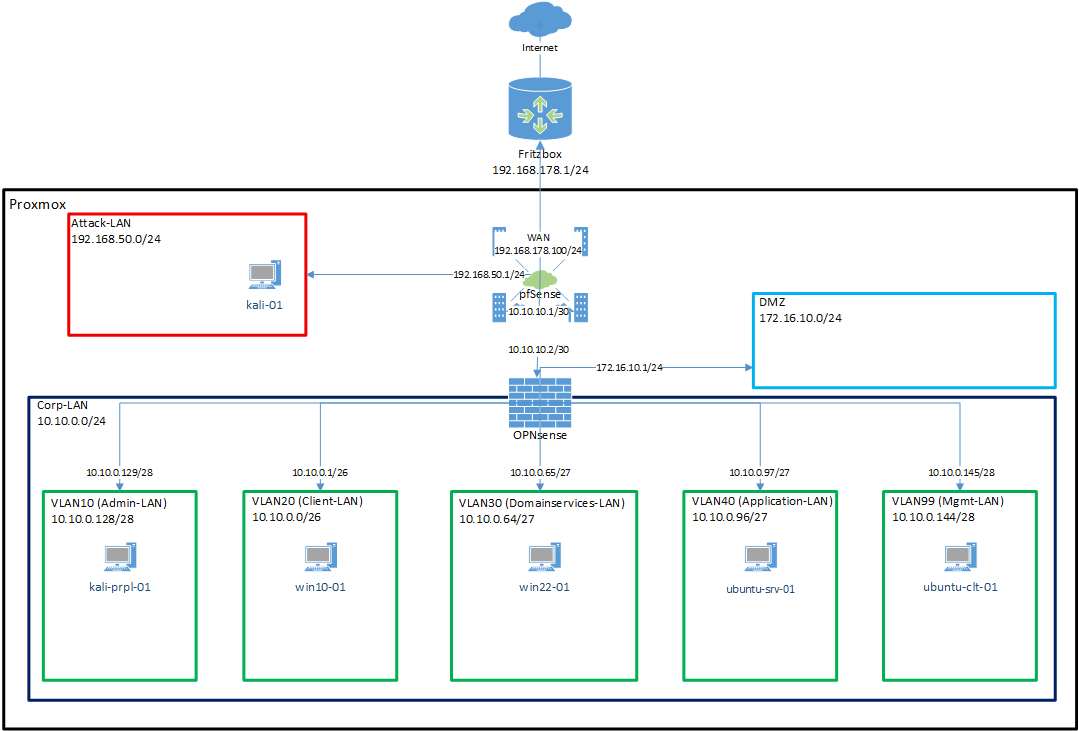
¶ 3. Architecture Overview
¶ 4. Future Plans
This home lab is still evolving. The following items are planned for future implementation and exploration:
- Vulnerability Scanning – deploy a scanner (OpenVAS/Greenbone or Nessus) for recurring assessments
- Network Zones & Segmentation – refine VLANs, DMZs, inter-VLAN policies, and jump-host patterns
- High Availability & Failover – pfSense/OPNsense HA pairs, redundant gateways, Proxmox cluster basics
- Proxy (Forward & Reverse) – reverse proxy (Nginx/Traefik/HAProxy) for DMZ apps (TLS, ACME, rate-limit, mTLS); optional forward proxy (Squid) for egress control, caching, content filtering
- IDS/IPS & NDR – Suricata/Snort on OPNsense with tuned rulesets (ET Open/Pro), Zeek for protocol analysis, test inline IPS in select VLANs, SPAN/mirror port for network-wide monitoring
- VPN – implement secure remote access (WireGuard, OpenVPN, IPsec) and test site-to-site vs. client VPN setups with split-tunneling, MFA, and logging
- AI Agents & Automation – n8n + LLMs for alert triage, ticket drafting, IOC enrichment, playbook triggering
- Centralized Logging & SIEM – expand Wazuh/Splunk; normalize logs (syslog/Elastic) and build detections/use-cases
- Monitoring & Alerting – Prometheus + Grafana (host/VM/service metrics), alert rules, blackbox probing
- Vulnerability Labs – DVWA, Juice Shop, Metasploitable, intentionally vulnerable AD apps for purple-teaming
- Threat Intelligence Feeds – MISP/OSINT ingestion, auto-enrich alerts with TI context and sightings
- Honeypots & Deception – deploy honeypots (Cowrie, Dionaea, T-Pot) in DMZ or internal zones to capture attacker TTPs and practice SOC alerting/analysis
- Backup & Disaster Recovery – scheduled Proxmox VM backups, pfSense/OPNsense config backups, test restores, offsite replication
- NAS/SAN Storage – add network storage (TrueNAS, FreeNAS, or Ceph) for central VM storage, snapshots, and redundancy; experiment with iSCSI, NFS, and ZFS
- Docker & Containerization – run services in Docker Compose stacks, build secure images, automate deployments
- Kubernetes – set up a small K8s cluster (e.g., k3s or kubeadm) for container orchestration, ingress, service mesh, and cluster security experiments
- PKI & Certificate Management – create an internal CA, issue TLS certs, test ACME automation and cert-based auth
- Mail & Messaging Lab – set up a simple mail relay (Postfix/Dovecot) and test phishing defenses, DKIM/SPF/DMARC
- Secrets Management – deploy Vault or Kubernetes Sealed Secrets for secure handling of keys and credentials
- DevSecOps Pipelines – integrate GitLab CI/Jenkins pipelines with container scans, IaC checks, and policy enforcement
- Endpoint Security – deploy Wazuh agents, Velociraptor, or OSQuery for endpoint visibility and incident response
- Load Balancing & Service Mesh – HAProxy/Traefik for L7 balancing; experiment with Istio or Linkerd in K8s
- Cloud/Hybrid Integration – small Azure/AWS extension (site-to-site VPN/WireGuard), hybrid identity lab
- Compliance & Hardening – CIS baselines for Linux/Windows, firewall hardening checklists, secure defaults
This section will grow over time as new goals and experiments are defined.